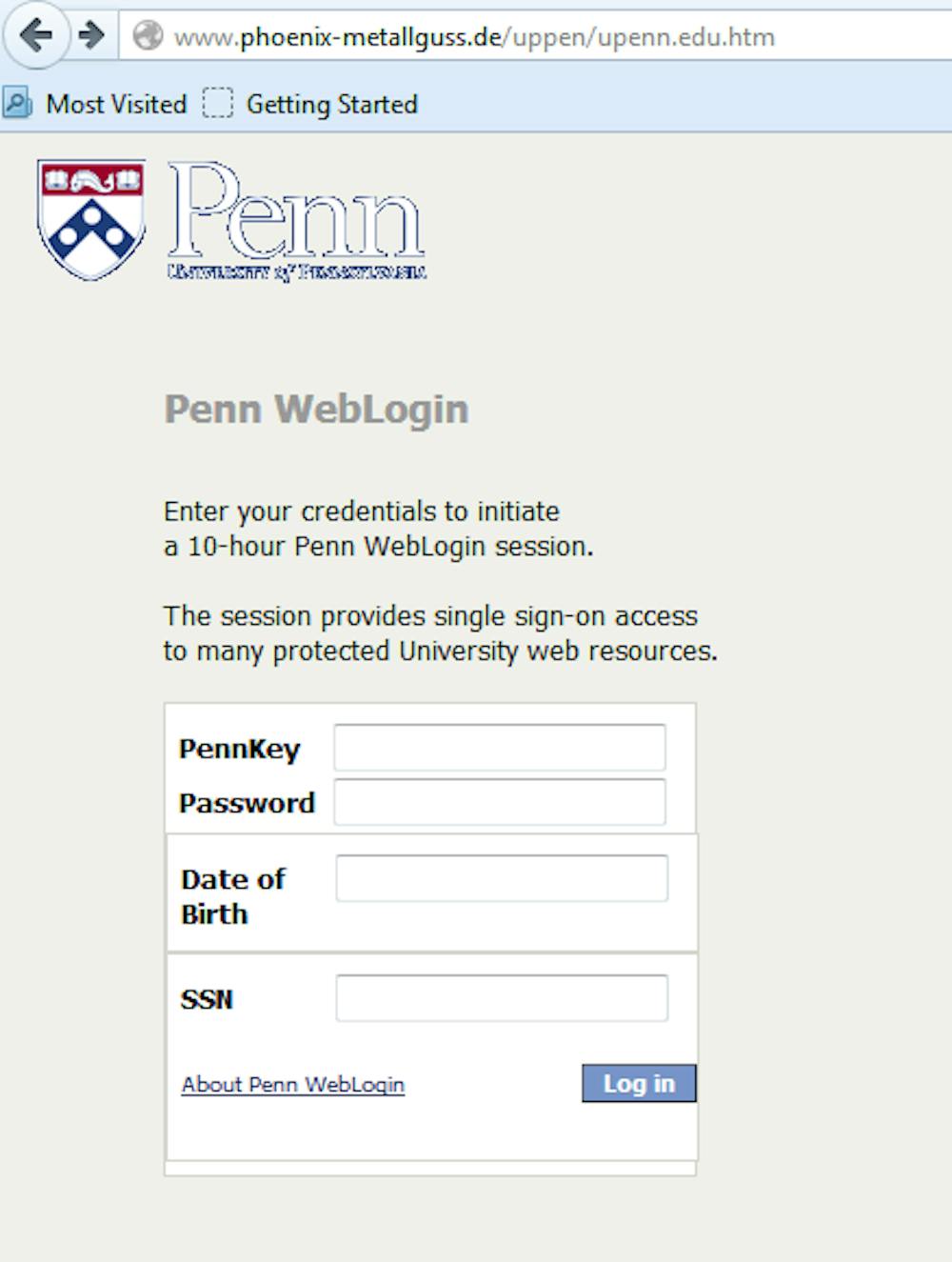
Approximately a dozen PennKey holders were affected by a phishing scheme designed to extract personal information that has been circulating over email in the past few days.
The scheme — detailed in an email from Information Systems & Computing — looks similar to a secure Penn login screen. It asks for users’ PennKey, password, date of birth and Social Security number.
ISC keeps a sample list on its website of confirmed email messages “targeting Penn services, or posing particularly large risk.” As of press time, there have already been four this month and just under 50 in 2013. The emails’ subject lines range from “Letter from the University of Pennsylvania: Penn” to “University Web Alert!” to “Password Validation.”
ISC’s email instructs those who receive an email with a link to the phishing form to close their browsers and send the link to ISC’s office. Those who already received the email and entered their actual information should immediately change their PennKey password and inform ISC.
University Information Security Officer Joshua Beeman said ISC has several programs in place to protect Penn affiliates against these phishing schemes. The office is piloting a service called “SafeDNS” that would proactively stop participating computers and offices from accessing websites ISC knows to be problems.
“If we know a phisher is using a website to collect information, we can often add their domain to the list of sites that SafeDNS blocks,” he said. “That was the case for this phishing attempt.” Those organizations participating in the pilot would have been protected from this attack after the phisher’s domain was added to ISC’s list.
ISC already uses an Intrusion Detection System to monitor for “pre-defined patterns of bad traffic,” which then sends an alert to ISC if it finds the pattern. This time, a rule was created to alert ISC if Penn user credentials were being sent to an attacker’s website.
If ISC is able to identify any information that makes a criminal prosecution possible, Beeman added, then they will work closely with law enforcement. However, the sheer magnitude of phishing schemes and systems makes it nearly impossible to identify any individual or group of specific phishers.
“The attackers are trying to gain credentials that would allow them specific access to Penn applications such as My Tax and My Pay, possibly for identity theft as well as to have your paychecks sent to another banking account you don’t own,” warned ISC’s email.
Anyone who receives the scam email or is unsure about whether an email they receive is legitimate is encouraged to contact ISC at security@isc.upenn.edu.